ANOTHER SUPPLY-CHAIN ATTACK —
Compromised update mechanism for Passwordstate pushes malware that steals data.
Dan Goodin
–

Getty Images
As many as 29,000 users of the Passwordstate password manager downloaded a malicious update that extracted data from the app and sent it to an attacker-controlled server, the app-maker told customers.
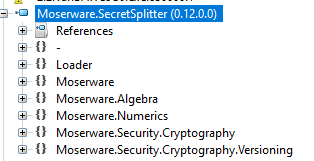
In an email, Passwordstate creator Click Studios told customers that bad actors compromised its upgrade mechanism and used it to install a malicious file on user computers. The file, named “moserware.secretsplitter.dll,” contained a legitimate copy of an app called SecretSplitter, along with malicious code named “Loader,” according to a brief writeup from security firm CSIS Group.
CSIS Group
The Loader code attempts to retrieve the file archive at https://passwordstate-18ed2.kxcdn[.]com/upgrade_service_upgrade.zip so it can retrieve an encrypted second-stage payload. Once decrypted, the code is executed directly in memory. The email from Click Studios said that the code “extracts information about the computer system, and select Passwordstate data, which is then posted to the bad actors’ CDN Network.”
The Passwordstate update compromise lasted from April 20 at 8:33 am UTC to April 22 at 12:30 am. The attacker server was shut down on April 22 at 7:00 am UTC.
The dark side of password managers
Security practitioners regularly recommend password managers because they make it easy for people to store long, complex passwords that are unique to hundreds or even thousands of accounts. Without use of a password manager, many people resort to weak passwords that are reused for multiple accounts.
The Passwordstate breach underscores the risk posed by password managers because they represent a single point of failure that can lead to the compromise of large numbers of online assets. The risks are significantly lower when two-factor authentication is available and enabled because extracted passwords alone aren’t enough to gain unauthorized access. Click Studios says that Passwordstate provides multiple 2FA options.
The breach is especially concerning because Passwordstate is sold primarily to corporate customers who use the manager to store passwords for firewalls, VPNs, and other enterprise applications. Click Studios says Passwordstate is “trusted by more than 29,000 Customers and 370,000 Security and IT Professionals around the world, with an install base spanning from the largest of enterprises, including many Fortune 500 companies, to the smallest of IT shops.”
Another supply-chain attack
The Passwordstate compromise is the latest high-profile supply-chain attack to come to light in recent months. In December, a malicious update for the SolarWinds network management software installed a backdoor on the networks of 18,000 customers. Earlier this month, an updated developer tool called the Codecov Bash Uploader extracted secret authentication tokens and other sensitive data from infected machines and sent them to a remote site controlled by the hackers.
First-stage payloads uploaded to VirusTotal here and here showed that at the time this post was going live, none of the 68 tracked endpoint protection programs detected the malware. Researchers so far have been unable to obtain samples of the follow-on payload.
Anyone who uses Passwordstate should immediately reset all the stored passwords, particularly those for firewalls, VPNs, switches, local accounts, and servers.
Representatives from Click Studios didn’t respond to an email seeking comment for this post.

