Why it matters: Last month, QNAP faced a security crisis when a ransomware group targeted its customers’ network-attached storage (NAS) devices. It issued a security update that remediated the problem. However, the fix caused unexpected side effects for some.
Taiwan-based QNAP Systems has had to explain how and why it forced some of its customers to update the software for their NAS systems. While there was a clear need to stop ransomware that had already reached thousands of QNAP storage systems, many users felt they should have been given a choice due to each one’s unique situation.
The issues started in January when the Deadbolt ransomware group began infecting QNAP devices with encryption malware. According to Malwarebytes, Deadbolt offered each affected user a decryption key for 0.03 bitcoin (about $1100). At the same time, it also tried to sell QNAP a universal decryption key and the details of the zero-day exploit Deadbolt used for 50 bitcoins (almost $2 million).
Towards the end of January, after issuing a warning to its users, QNAP issued an automatic security update that addressed the exploit. However, it did it in a way that updated some users’ systems even if they had disabled auto-update, which angered some.
Some users may have been running crucial processes, which the auto-update might have interrupted. Some of the ransomware victims who had paid the ransom but got the update before decrypting their files could no longer use the keys they got from Deadbolt. More recent versions of QNAP’s software may have also broken other functionalities.
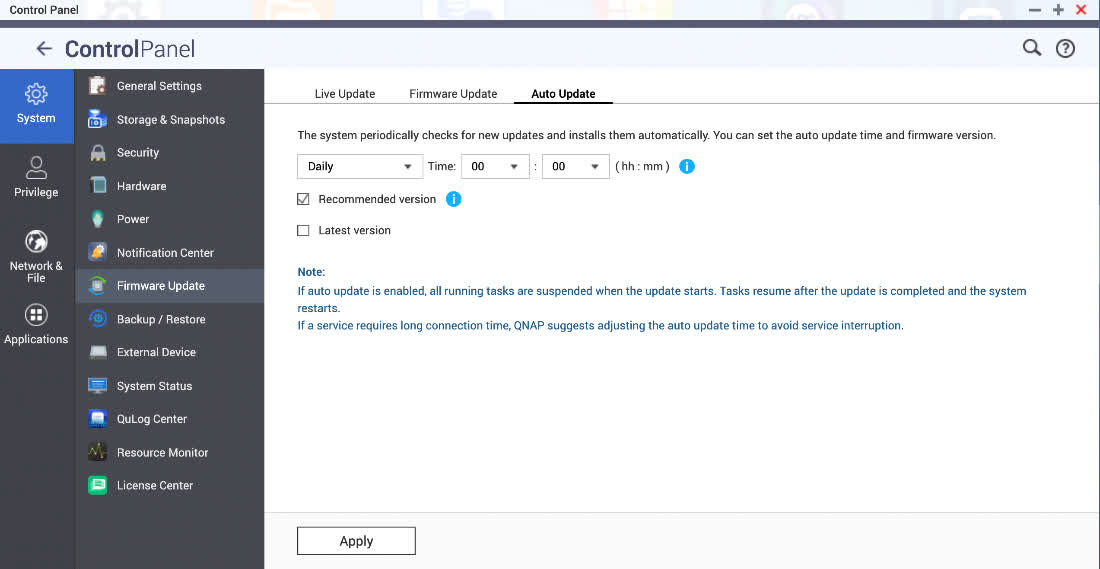
The global updating was allowed because QNAP has two levels of auto-updates: a setting to keep a system updated to the latest build and one to keep it updated to a “recommended version.” The company issued the security update by changing which iteration was recommended. Some users who went through multiple system updates in succession may have disabled auto-updating to the latest version but not known about the auto-updates to the recommended build.
This system is designed to provide flexibility, but tech companies usually respond to similar problems by simply telling users about a security update and strongly recommending they apply it. At least in that way, users would have retained control of how and when the software was updated.

