At least someone is buying Pixel phones —
FBI honeypot phones are now public—and showing up on the secondary market.
Ron Amadeo
–
The Anom login screen, which was hidden in the calculator app. Note the cool “hacker”-style logo.
If your device ever shows this message during boot and you didn’t unlock the phone yourself, run, or throw it in a lake, or blow it up. Whatever you do, don’t give it your credentials.
The ArcaneOS boot screen.
Last month, authorities disclosed that the FBI and Australian Federal Police secretly operated an “encrypted device company” called “Anom.” The company sold 12,000 smartphones to criminal syndicates around the world. These were pitched as secure devices but were actually honeypot devices that routed all messages to an FBI-owned server. The disclosure was light on details, but now that it’s public, Anom phones are being unloaded on the secondary market. That means us normal people are finally getting a look at them, starting with this Vice article detailing one of the devices.
The FBI has basically weaponized what the Android modding community has been doing for years. Some Android phones have unlockable bootloaders, which let you wipe out the original operating system and replace it with your own build of an OS, called a custom ROM. The Anom device Vice got was a Google Pixel 4a, one of the most developer-friendly devices out there. The FBI’s custom ROM shows an “ArcaneOS” boot screen, and it replaced the normal Google Android distribution with the FBI’s skin of Android 10.
The FBI’s sales pitch to alleged criminals was that these were security-focused devices (so please use them to document your illegal activities!), and that involved a lot of fun security theater. A “pin scrambling” feature would swap around the order of the lock screen numbers so that no one could guess your code from screen smudges.
Two different interfaces would launch depending on what PIN you typed in on the lock screen. PIN one would show a bunch of popular but non-functional apps, like Tinder, Instagram, Facebook, Netflix, and Candy Crush. Presumably, this was meant to fool any third parties checking out your phone.
A second PIN would enter what was supposed to be the secure section of the phone, showing three apps: a clock, calculator, and the settings. From here, the “calculator” app actually opened a login screen to Anom, which targets were told was a secure, encrypted way to chat. This was basically the smartphone equivalent of a fake book triggering a bookshelf to slide over, revealing a secret passage. It’s so secret, it has to be secure!
With the new knowledge that the FBI phones presented themselves as “ArcaneOS” to users, Vice was able to find several other confused users on the internet who apparently ended up with second-hand FBI devices. Here’s a forum post from XDA Developers user “mayday175” asking how to fix their recently purchased, second-hand Pixel 4a with a barely functional build of “ArcaneOS” locked in place. Because nobody had ever heard of this bizarre OS, the user posted a treasure trove of screenshots in an attempt to get help. Mayday writes, “The installed OS is ArcaneOS 10. The system updater says that ArcaneOS 11 is available for download (but I don’t want to do that in case it makes this thing even harder to fix).” I wonder how good the FBI is at delivering timely Android OS updates?
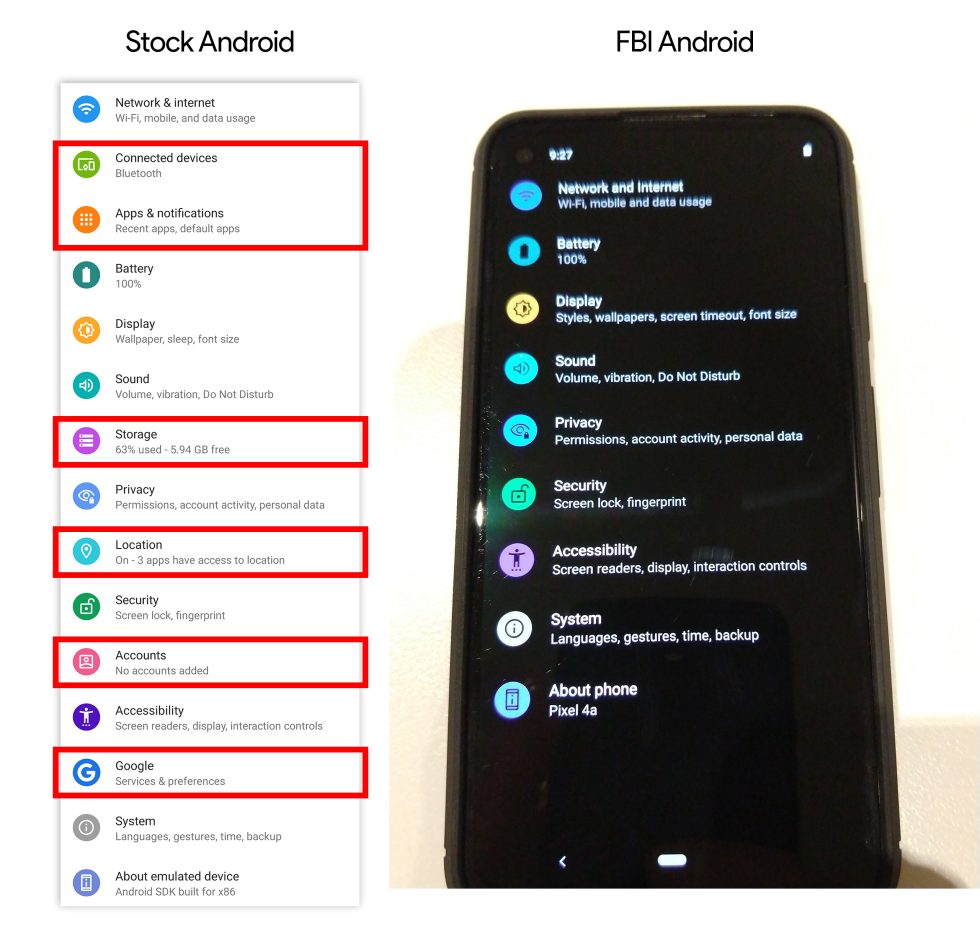
Enlarge / The FBI stripped out a lot of settings that would allow users to look into the phone guts or control things like location.
Ron Amadeo / Mayday175
The FBI’s compromised phones definitely show some red flags that a tech-savvy user should be able to spot. When you start up an Android phone, the first check that happens is Verified Boot, which makes sure the operating system is cryptographically signed by your device manufacturer, ensuring it hasn’t been tampered with. If a device fails verified boot, either from having an unlocked bootloader or a re-locked bootloader with tampered software, it will show a message during startup. In this case, the FBI devices display a message saying, “Your device is loading a different operating system,” complete with a yellow exclamation point icon and a link for a Google support page at g.co/ABH. This message is very important.
Like the support page says, if you did this yourself to install a custom ROM or to root your device, it’s no big deal, but if you don’t know why this message is appearing on your device, that’s a huge problem and you should definitely not use the phone. I can’t overstate how big of a deal this message is. Verify Boot is “step one” for any and all phone security, and this message indicates that it’s compromised. While showing this message, Android will add a 10-second delay to the boot process, and there’s even a “Press power button to pause” message on this screen—because you’re supposed to abort the boot sequence if you suddenly see this message.
Normally, the right way to fix a compromised device like this is to download a clean, official system image from Google, wipe out the unknown OS, and install regular Google Android. Several users report that wouldn’t work in this case. ArcaneOS doesn’t let users into the Developer Options to unlock the bootloader, so once the FBI unlocks the bootloader, flashes Arcane OS, and locks the bootloader, you’re pretty much stuck with ArcaneOS. This is a malicious operating system.
The FBI changed quite a bit of the core Android OS, stripping out helpful Android settings that might reveal the device’s true nature. The system settings for apps, storage, and accounts have been removed. There’s now no way to see a list of all the installed system apps, where users might spot something suspicious like “FBI_Spyware.APK.” What’s installed on the phone is a black box. The FBI also wiped out the “Location” settings, probably in an attempt to stop users from turning off GPS tracking.
If you aren’t interested in having a group chat with the FBI and some targeted criminals, the phones don’t seem very useful. They don’t have the Play Store or any other Google apps, and other than a clock and the calculator app that leads to this compromised chatting app, it doesn’t sound like any other apps worked.
I’m sure this won’t be the last we hear of Anom and Arcane OS. Now that the word is out, and with something like 12,000 devices out there, it’s probably only a matter of time before the Android modding community has a full dump of the FBI’s Android skin. Who wants to install it?
Listing image by Vice
