A hot potato: When talking about “abuse” in relation to popular instant messaging service Discord, it’d usually be about the group chat platform being used by trolls or for hateful and NSFW content. But Discord’s content delivery network (CDN) is now increasingly being used to host malicious files and hand out malware through links that seem legitimate.
A report by Sophos has exposed the scale and variety of malware using the Discord’s CDN: “Sophos products detected and blocked, just in the past two months, nearly 140 times the number of detections over the same period in 2020,” said authors Sean Gallagher and Andrew Brandt, with 17,000 unique URLs found pointing to malware in the second quarter of 2021.
And those 17,000 URLs are only counting malware hosted by the service, which keeps files on Google Cloud and uses Cloudflare as a frontend. The vast figure excludes malware hosted elsewhere that makes use of the infrastructure provided by the CDN; Discord’s chatbot APIs have been used for command-and-control of malware in infected targets, as well as for exfiltrating stolen data into private servers.
Malware using the platform varies, but according to the authors the majority of it is centered around data theft, either through direct credential-stealing or remote access trojans (RATs). Threats targeting Android platforms were also seen, ranging from ad-clickers to banking Trojans, as well as expired ransomware that lacked any way to pay the attackers.
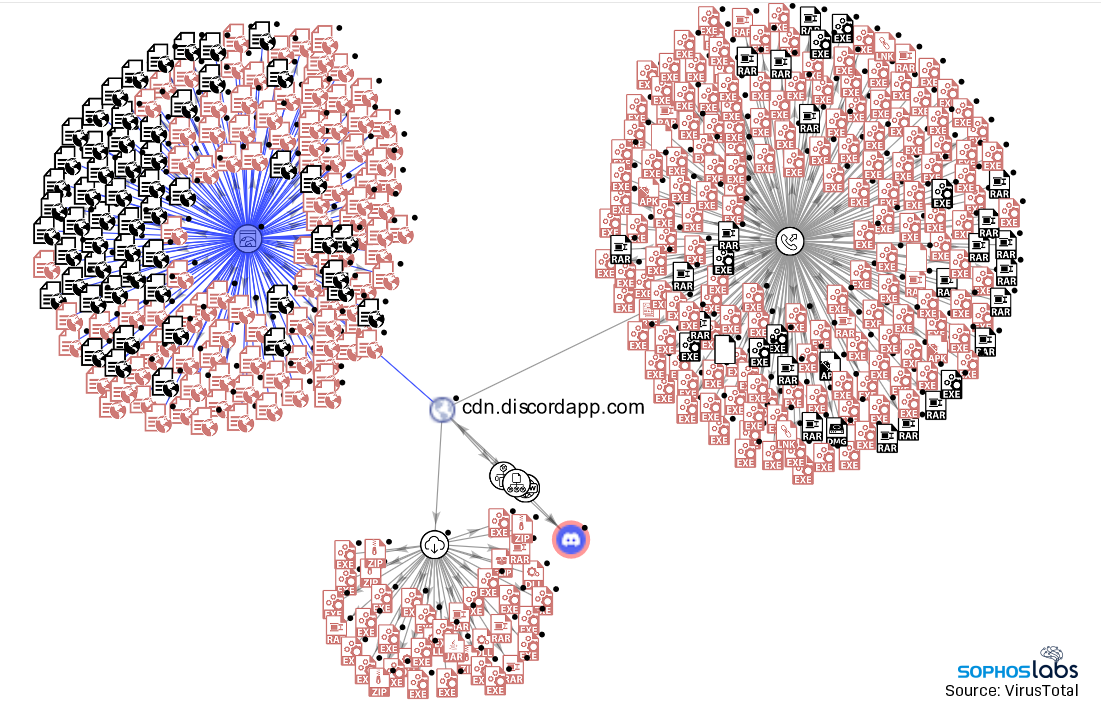
Visualization of a small portion of malicious (red) and benign (black) files hosted on Discord’s CDN.
Discord is a popular messaging platform that was originally targeted at gaming communities, and they continue to have a substantial presence on the platform, so it’s not surprising that a lot of the malicious files hosted and distributed on it are tied to gaming.
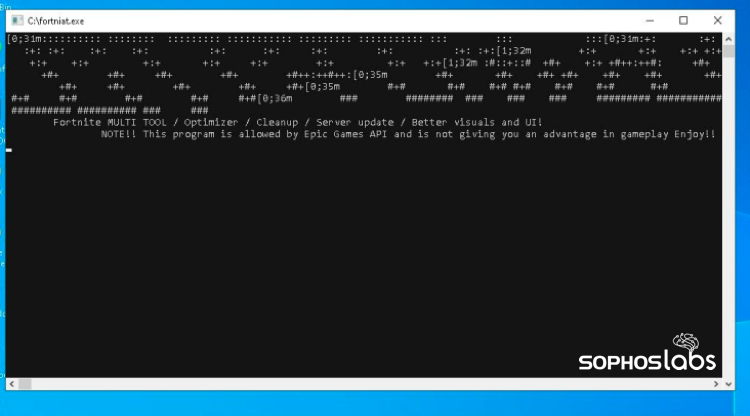
For example, researchers identified a modified Minecraft installer that also captured keystrokes, screenshots, and camera images, as well as a “multitool for FortNite” (sic) that infected systems with a Meterpreter backdoor.
Others targeted Discord itself, stealing credentials and authentication tokens, or disguised themselves as software ranging from private browsers to cracked Adobe applications.
Social engineering was also often a factor, with the promise of generating keys for Discord’s premium Nitro service commonly used to bait users. One example immediately attempted to find and kill off processes for dozens of security tools, as well as built-in Windows protection features — although if it’s any consolation, like the aforementioned ransomware, many of these trojans were old enough that they were trying to phone home to servers that weren’t around to respond.
Ultimately, the freemium model that Discord relies on for its accessibility works against it here. While many quality-of-life features desirable to benign users are paywalled behind Nitro, free accounts are still fully able to upload files (albeit with a size limit) and communicate with its APIs.
This allows threats to pop up time and time again with new accounts; while Discord took down much of what was identified by the researchers, they found that new malware was continually being uploaded or communicating with Discord.

